At first blush, you might be wondering why anyone would need to scan a Linux server for malware.
Selected by Galigio via Computer Borders

At first blush, you might be wondering why anyone would need to scan a Linux server for malware.
Selected by Galigio via Computer Borders
Opera today launched version 50 of its desktop browser. Sadly, this release doesn’t come with a cake to celebrate this milestone (not even a tiny cupcake), but the newest release does include a new feature that makes sure that nobody can mine crytocurrencies in your browser.
In Opera, this new cryptojacking feature is automatically enabled when you turn on the browser’s ad blocking tool.
from https://is.gd/kA4S26
Selected by Galigio via Computer Borders
For years, TrueCrypt was the encryption tool of choice for Linux users. It worked well, and it did everything you could ever want. Then one day, the project was discontinued. Ever since then, Linux users have been scrambling to find an encryption tool that works as well.
For most, the best tool to use is VeraCrypt. The main reason that VeraCrypt stands out from the rest of the new encryption tools is that it is a “fork” from the old TrueCrypt code. This means if you’ve used TrueCrypt for years but want something that is actively maintained, you can install VeraCrypt on Linux and everything will continue to work.
from https://is.gd/HFNBWZ
Selected by Galigio via Computer Borders
The five statements below are the causes behind a lot of computer security risk and exploits. If you understand them well enough today, you will be ahead of your peers.
from https://is.gd/4zaJnw
Selected by Galigio via Computer Borders
The effect of geopolitics on cybersecurity can be seen daily – from Chinese cyber espionage to Russian attacks on the Ukraine and North Korea’s financially-motivated attacks against SWIFT and Bitcoins – and, of course, Russian interference in western elections and notably the US 2016 presidential election.
The primary cause is political mistrust between different geopolitical regions combined with the emergence of cyberspace as a de facto theater of war.
Selected by Galigio via Computer Borders
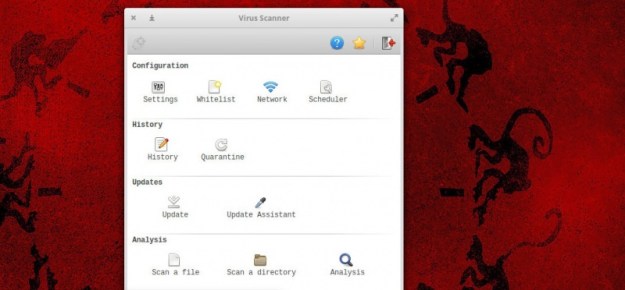
Wait, Linux needs antivirus and anti-malware solutions? I thought it was immune to such things. Perhaps a bit of clarification is necessary here. First and foremost, no operating system is 100 percent immune to attack. Whether a machine is online or offline, it can fall victim to malicious code.
Although Linux is less prone to such attacks than, say, Windows, there is no absolute when it comes to security. I have witnessed, first hand, Linux servers hit by rootkits that were so nasty, the only solution was to reinstall and hope the data backup was current. I’ve been a victim of a (very brief) hacker getting onto my desktop, because I accidentally left desktop sharing running (that was certainly an eye opener). The lesson? Even Linux can be vulnerable.
from https://is.gd/VLyo98
Selected by Galigio via Computer Borders
Firewalls represent the technological gateways into and out of companies, as well as serving to compartmentalize internal systems and networks to segregate them from one another.
Network traffic flowing through, or blocked by, firewalls does so based upon specific permissions intended to secure systems, services and users from unauthorized access or malicious threats.
A properly maintained firewall is one of the keys to business and operational success.
from https://is.gd/DwBX47
Selected by Galigio via Computer Borders
The VPN (Virtual Private Network) server provides the network technology that will allow us to extend the reach capabilities of our local network over the Internet, a great example of this would be the possibility for two branches to communicate using the internet as the sole means.
from https://is.gd/9h1dpn
Selected by Galigio via Computer Borders
Google runs lots of different systems, and they all store data about you. There’s the search engine itself, of course, which knows what you’ve been looking for on the web. Then there’s Youtube, Blogger, Calendar, your Google Drive, Hangouts, Gmail and more.
If you want to download a copy of all the data about you that’s held on Google’s servers, it’s actually surprisingly easy.
from https://is.gd/jzuEd0
Selected by Galigio via Computer Borders
Objective Install Firejail and use it to sandbox applications, like web browsers, that interact with the open Internet. Distributions This will work with any current Linux distribution. Requirements A working Linux install with root privileges.
from https://is.gd/ACXgFa
Selected by Galigio via Computer Borders