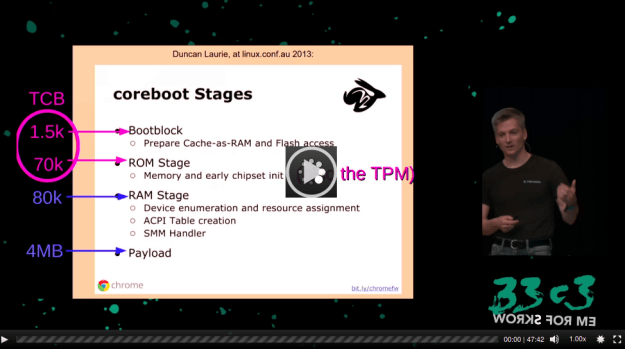
If you use TAILS you are certainly interested to better know HEADS because Heads isn’t simply another Linux distribution, it merges physical hardening of particular hardware platforms and flash protection attributes with a Linux boot loader in ROM as well as custom Coreboot firmware.
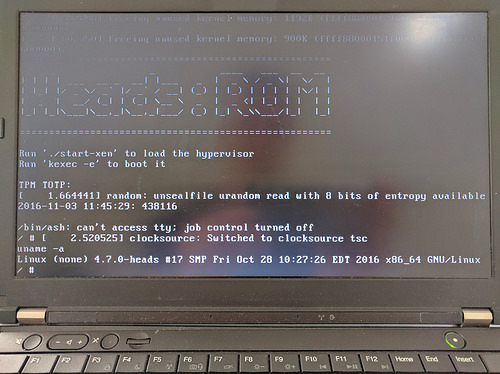
The key factor in Heads is represented by its steady monitoring of the boot process that allows detecting if the firmware has been changed by malware.
If this first check certifies that all is unchanged, heads uses the TPM as a hardware key to decrypt the hard disk.
The certified integrity checking of the root filesystem is really effective against exploits but it doesn’t secure the system against each possible attack but it is able to effectively divert many types of attacks against the boot process and physical equipment that have usually been ignored in conventional setups, hopefully increasing the issue beyond what most attackers are willing to spend.